Innovative Intelligent Cybersecurity Solution
Harnessing AI to defend against real-world threats, cyber threats and fraud
Advanced Security
Intelligent, innovative, and robust powered security solutions to protect your critical infrastructure and sensitive data from evolving cyber threats.
Cyber Intelligence
Proactive threat intelligence and monitoring services to identify vulnerabilities and prevent security breaches before they impact your business operations.
Industry Certified
Our security experts hold top industry certifications and follow best practices to deliver comprehensive cybersecurity solutions tailored to your needs.
Complete Website Security
Protect your business from online threats with our advanced website security solutions. We provide real-time monitoring, proactive threat detection, and powerful protection against malware, hackers, and data breaches to keep your digital assets safe.
Malware Detection & Removal
Our system scans your website 24/7 to detect and remove hidden malware, preventing unauthorized access and protecting customer data.
Content Delivery Network (CDN)
Accelerate website performance and strengthen security with our global CDN that filters malicious traffic and ensures lightning-fast loading.
24/7 Cyber Security Support
Our experts are available round-the-clock to respond to threats, provide guidance, and ensure your website remains fully protected.
Managed Web Application Firewall
Defend your site from DDoS attacks, SQL injections, and other vulnerabilities with our intelligent firewall managed by security professionals.

Our Approach To Security
We believe security should be built into every layer of your digital ecosystem. Our proactive approach combines advanced technologies, compliance frameworks, and continuous monitoring to safeguard your business from evolving cyber threats.
-
Secure By Design
From the ground up, we integrate security into every stage of development and infrastructure. This ensures your applications and systems are resilient against vulnerabilities and threats.
-
Compliant By Design
Our solutions align with global standards such as GDPR, ISO 27001, and PCI-DSS, helping your business stay compliant while maintaining strong security practices.
-
Continuous Monitoring
We provide 24/7 surveillance of networks and applications, instantly detecting suspicious activity to mitigate risks before they become real threats.

Cybersecurity Solutions
Comprehensive cybersecurity services designed to protect your digital assets, identify vulnerabilities, and strengthen your security posture with advanced threat intelligence and proactive defense mechanisms.
Cyber Intelligence
Leverage advanced AI-driven threat intelligence to predict, detect, and neutralize cyber risks before they strike. Our intelligence framework monitors global attack patterns, dark web chatter, and behavioral analytics to deliver real-time insights that empower proactive defense.
Vulnerability Assessment
Identify weaknesses before attackers do. Our vulnerability assessments combine automated scanning and manual testing to uncover configuration flaws, outdated software, and hidden security gaps—providing a prioritized roadmap for remediation and risk reduction.
Penetration Testing
Simulate real-world cyberattacks to evaluate your organization’s resilience. Our ethical hackers assess your applications, networks, and systems to expose exploitable vulnerabilities and provide actionable mitigation strategies that strengthen your overall security posture.
Forensics
Investigate and understand security incidents with precision. Our digital forensics experts trace breaches, recover compromised data, and provide detailed incident reports. We also help organizations maintain compliance with standards like GDPR, ISO 27001, and PCI-DSS to ensure trust and accountability.
Incident Response
When every second counts, our rapid response teams act immediately to contain, eradicate, and recover from security breaches. From root-cause analysis to post-incident optimization, we ensure minimal damage, downtime, and data loss.
DevSecOps Implementation
Integrate security into every stage of your software development lifecycle. Our DevSecOps experts embed automated security checks, continuous monitoring, and vulnerability management into CI/CD pipelines—empowering teams to innovate securely and efficiently.
Ransomware Incident Response
Enalytechs has the finest talent in Malware Analysis and Incident Response. Our team rapidly identifies ransomware attacks, minimizing damage and securing affected systems to prevent further compromise.
By leveraging cutting-edge detection tools and real-time threat intelligence, we ensure early identification of malicious activity before it can spread across your infrastructure.
With years of expertise, we have successfully handled multiple critical national and international cybersecurity incidents. Our advanced forensics and malware analysis uncover attack vectors with precision.
We provide detailed incident reports, helping organizations understand how the attack occurred and offering actionable recommendations to strengthen defenses against future breaches.
Our Ransomware Evasion strategies block further spread of malicious payloads, isolating compromised systems and protecting unaffected assets in real-time.
We implement immediate containment measures such as network segmentation, privilege restriction, and system isolation to ensure business-critical operations remain secure.
On multiple occasions, our expert Negotiation Teams have successfully engaged with threat actors to recover critical client data and reduce financial impact.
Every negotiation is handled with confidentiality and precision, ensuring that our clients achieve the safest possible outcome while avoiding unnecessary financial loss.
During and post-compromise, we focus on rapid recovery. Our proven methods restore operations quickly, ensuring business continuity while preventing future attacks.
Beyond recovery, we also implement long-term resilience strategies such as backup validation, employee awareness training, and infrastructure hardening to minimize the risk of future compromises.

Complete And Effective Protection For Your Home And Office
Safeguard your personal and professional spaces with our end-to-end cybersecurity and digital protection solutions. From proactive threat detection to 24/7 expert support, we ensure your systems remain secure, reliable, and resilient.
Check And Search Hazards
We perform in-depth risk assessments and vulnerability scans to identify potential threats before they impact your digital environment, ensuring peace of mind and stronger security.
Install and Configure Software
Our experts install and configure advanced security tools, firewalls, and antivirus systems to protect against malware, ransomware, and unauthorized access.
Departure of the Our Experts
When critical issues arise, our certified specialists provide rapid on-site response to contain threats, secure systems, and restore business continuity.
24/7 Support and Remote Admit
Our team is available round-the-clock to monitor, troubleshoot, and resolve incidents remotely, keeping your home and office protected at all times.

What Client’s Say About Us
Trusted by leading organizations worldwide, we deliver exceptional cybersecurity solutions that protect against evolving threats. Here's what our clients say about their experience with Enalytechs.
Enalytechs saved our company from a major ransomware attack. Their incident response team was professional, quick, and helped us recover all our data without paying the ransom. Highly recommended!

Sarah Chen
IT DirectorTheir AI-powered threat detection system identified vulnerabilities in our network before any damage occurred. The 24/7 monitoring service gives us complete peace of mind. Outstanding cybersecurity expertise!

Michael Rodriguez
CEOEnalytechs conducted a comprehensive security audit for our financial institution. They identified critical vulnerabilities and provided detailed recommendations. Their expertise in blockchain security is unmatched.

David Thompson
Security ManagerWorking with Enalytechs transformed our cybersecurity posture completely. Their OSINT analysis helped us understand our threat landscape better, and their proactive approach prevented multiple potential breaches.

Emily Johnson
CISOThe penetration testing services from Enalytechs revealed security gaps we never knew existed. Their ethical hacking approach and detailed reporting helped us strengthen our defenses significantly.

Robert Wilson
Operations ManagerEnalytechs provides exceptional cybersecurity consulting services. Their team's expertise in AI-powered security and threat intelligence helped modernize our entire security infrastructure. Truly innovative solutions!

Lisa Anderson
Technology Director24/7 Cybersecurity Operation Center
With advanced AI-powered analytics and expert security analysts, we deliver proactive defense and real-time incident response to keep your business secure 24/7/365.
- Managed Web Application
- SIEM Threat Detection
- Content Delivery Network
- 24/7 Hours services
- Security Management
- Instant Malware Removal
- Free Delivary Services
- Website Hack Repair
- Website Security Services
- Provide Security services
Latest News From Blog
Discover the essential security practices your business must implement this year.

Securing Remote Work Environments
Learn the best practices to protect sensitive data while working remotely.

How AI is Revolutionizing Cybersecurity
Explore how artificial intelligence is detecting and preventing cyber threats faster.

Effective Response to Data Breaches
Learn step-by-step how organizations can quickly detect, contain, and recover from data breaches.
Solution Overview
Following Services are included as Part of Vulnerability Assessment Cycle
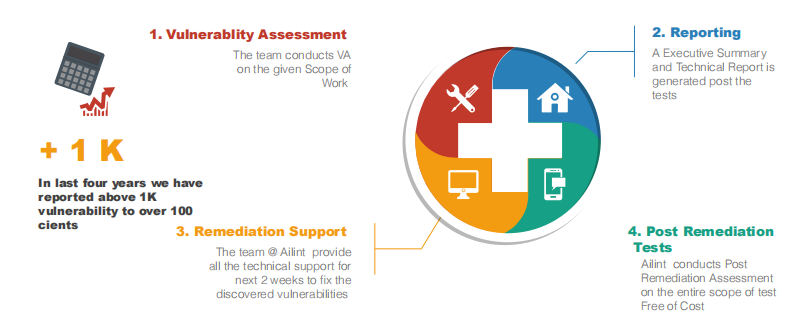
Hierarchical Approach to VA Tests
Our structured security assessment methodology ensures comprehensive coverage across all vulnerability vectors.
- Vulnerability Assessment - Systematic scanning and identification of security weaknesses
- Penetration Testing - Simulated attacks to validate security controls
- Security Monitoring - Continuous surveillance of network traffic and system activities
- Incident Response - Rapid containment and remediation of security breaches
- Post-Remediation - Verification of implemented security measures







